CMS Information Security Acceptable Risk Safeguards (ARS) v2.0 to v3.0
CMS has recently moved from ARS v2.0 to v3.0 and have taken off v2.0 from their public website. If you need a copy of moderate ARS v2.0 get it here.
Cloud Security Evanglist
IT Security practitioner with a deep interest in Cyber Security, Compliance, Cloud Security, Penetration testing, Big Data Analytics, Cloud Automation (Puppet), Computer Forensics toolkits, Converged and Hyper-Converged infrastructure. In my free time, I like riding my motorcycle on curvy roads while keeping an eye out for wildlife which might cut my ride short
Tuesday, March 14, 2017
Sunday, July 31, 2016
It is personal: When your life resides in a data center
How many
times did you leave your wallet at a park bench or public transport and slept
soundly knowing your money is in public domain? I guess not a lot of times. Why
is that when our most important health records, personal information and
financial information reside in an un-named data center we do not care and
assume it is safe secured by security experts?
The true picture is far more dire and
perilous. Data center operators are struggling with rapidly changing data
center architecture, declining budgets to hire security experts, ancient
perimeter firewall security and non-existent micro-segmentation inside the data
center network. DC operators need to
protect the high volume east-west traffic using virtual firewalls while
protecting the north-south traffic and intra-dc traffic via non-virtual, high
end perimeter firewalls.
Given below
are some methods we can use to secure our data within a data center;
1. Redundant data links within a
data-center which is fully covered by virtual firewalls.
2. Traffic between tenants should not
hit edge gateway routers. But should be directed internally from tenant to
tenant. Used by VMware NSX and Cisco ACI micro-segmentation solutions
3. Virtual firewalls should be scale up
and down depending upon amount of traffic.
4. Use traditional security like VLAN’s
to segment workloads according to job function.
5. There should be limited or no traffic
between different tenants within a data center.
6. Firewall rules for both edge and tenant
firewalls need to be intelligent and integrated with real time threat feeds.
The age of static signature based firewalls is almost at an end.
7. Compliance and Security policies
should be set on who can connect and have access to the data center.
8. The data center should have a one
pane view on all attacks successful or unsuccessful on the data center.
9. The data center should have separate
data paths for backup and continuity of operations solutions.
10. The data center should have
remediation policies in place.
11. The data center operator should
enable data encryption both per workload and on data residing at rest.
12. Workloads should always be encrypted
while they are moved from one city to another or from one continent to another.
13. Hard drives should remain encrypted
and non-useable in case of physical access and theft by insiders.
14. Servers should need to have TPM
secured startups preventing supply chain attacks.
15. Data centers need to be located in
secure locations and access granted to valid small list of employees.
16. Vendors and non-employees should not be
granted access and escorted at all times in case of need.
17. Regular scans to detect rogue
wireless access points and no photography and cell use should be permitted
within a data center.
18. Data center personal should be vetted
and have continuous monitoring to prevent against exploitation by criminal
gangs.
The items detailed above are just a starting
point of looking at how we can ensure our personal life data and information is
secured in the cloud. As our personal lives become more digital, the dangers of
our identity being stolen becomes more real as we have no control on how fast
our personal information moves around the world travelling from one data center
to another. Data center operators typically move virtualized work-loads to
various data centers around the world in matter of seconds. A virtualized
server with all our credit card information is routinely moved from Singapore
data center to Northern California data center while we sleep. It is important to
understand how our data is stored and what kind of security safeguards are
being taken to protect our data. Ignorance is bliss is not an option
anymore.
Thursday, April 21, 2016
Big Data
What are the three V's which define big data?
1. When your data Velocity is variable
2. When your data Variety is variable
3. When your data Volume is variable
When you have a tremendous amount of data composed of a large variety of objects like documents, pictures, videos, audio etc you know you have big data. Google first encountered Big Data when they cataloged the visible Internet. They had to create a Google file system which was distributed and a processing algorithm to process big data. In time Mr Cutting produced Hadoop and the rest is history.
Thursday, March 3, 2016
Why virtual job fairs make sense
Today I attended another by invitation job fair hosted by a few innovative companies. The virtual space has gotten even better and more easier to use than before.Virtual job fairs are a reliable method of recruitment and allow candidates and recruiters save on travel time and costs. The virtual job fairs allow candidates to chat with recruiters with the same frequency as an onsite job fair.
Wednesday, February 10, 2016
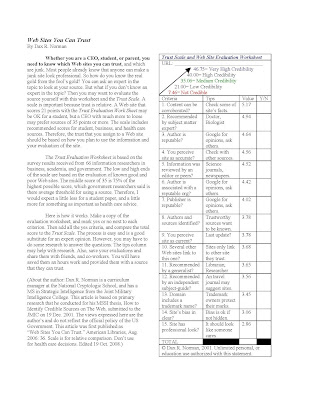
How to check if we trust a website
Dax Norman gave a very creative scoring method which could be used to check if a website can be trusted here and below.
Capabilities of IBM App Scan as a Source code scanning tool
Capabilities of IBM App Scan as a Source code scanning tool
I like IBM App Scan as it offers a wide variety of options and is a flexible enterprise tool. The pricing for IBM and HP tools are almost similar and most IT shops will have to invest in such tools incrementally.
AppScan Enterprise Server provides:
- Scalable, enterprise architecture
- Intelligent fix recommendations to ease the process of remediation after vulnerabilities have been found
- Ability to scan websites for both embedded malware and links to malicious or undesirablesites to ensure your website is not infecting visitors or directing them to unwanted or dangerous sites without their knowledge
- Continuous monitoring and aggregation of metrics to ensure remediation and trend improvement over time
- Addition of a web services API enabling integration with IBM Rational Insight
- Sophisticated dashboards and flexible reporting views to provide enterprise-wide visibility of risks and remediation progress. It offers the lowest false positive rate in the industry
- Ability to test sequential business logic, such as opening a new account or making an online
- purchase
- Over 40 out-of-the box security compliance reports including PCI Data Security Standard, Payment Application Data Security (PA-DSS), ISO 27001 and ISO 27002, HIPAA, GLBA and Basel II
- Role-based reporting access and scan permissions to help enforce test polices and to centralize vulnerability scanning
- Audit a large number of applications and triage results
- Communicate the identified issues to Development for remediation
- Monitor a large number of applications on an ongoing basis
- Create and communicate test policies to Development and QA teams
- Present application security risk reports to management
- Assess the security risk to your organization that your web applications present
- Identify the most problematic applications and take action
- Identify the types of issues that are most prevalent to create appropriate education programs
- Assess if the security of your web applications is improving
- Identify compliance risk related to various industry guidelines
Thursday, January 29, 2015
Barrier to entry for PCI gap analysis
If a company processes credit cards, and other payment cards they need to show compliance to PCI DSS stardards.
PCI gap analysis finds areas where a company does not meet the ~228 PCI DSS security controls/requirements and points out PCI DSS security controls which require remediation. PCI gap analysis activity is a lucrative business but the fees charged by PCI organization and the requirements keeps the barriers to entry in this market space quite high. Companies can perform self assessment questionnaire (SAQ) but they still need sign off from QSA certified auditors. Different type of vendors/companies require compliance to different sections and security controls listed in the PCI DSS standards.
PCI gap analysis finds areas where a company does not meet the ~228 PCI DSS security controls/requirements and points out PCI DSS security controls which require remediation. PCI gap analysis activity is a lucrative business but the fees charged by PCI organization and the requirements keeps the barriers to entry in this market space quite high. Companies can perform self assessment questionnaire (SAQ) but they still need sign off from QSA certified auditors. Different type of vendors/companies require compliance to different sections and security controls listed in the PCI DSS standards.
Tuesday, January 27, 2015
Old exploits new names aka Ghost vulnerabilities in Linux distros
Ghost vulnerability affecting Linux distributions remind us that we need to perform static code analysis and also keep fixing old code. We keep finding memory management exploits in code which should be already been fixed for example glibc. More on this vulnerability found here.
Monday, January 26, 2015
DoD Cybersecurity Policy Chart Has Been Updated
The latest information assurance (IA) policy chart looks pretty comprehensive. The latest IA Policy Chart can be found on the CSIAC website here.
As the webpage states "
The goal of the DoD Cybersecurity Policy Chart (downloadable via the hyperlinked icon below) is to capture the tremendous breadth of applicable policies, some of which many cybersecurity professionals may not even be aware, in a helpful organizational scheme. The use of color, fonts and hyperlinks are all designed to provide additional assistance to cybersecurity professionals navigating their way through policy issues in order to defend their networks, systems and data."
As the webpage states "
The goal of the DoD Cybersecurity Policy Chart (downloadable via the hyperlinked icon below) is to capture the tremendous breadth of applicable policies, some of which many cybersecurity professionals may not even be aware, in a helpful organizational scheme. The use of color, fonts and hyperlinks are all designed to provide additional assistance to cybersecurity professionals navigating their way through policy issues in order to defend their networks, systems and data."
Sunday, January 25, 2015
Dangers of doing business in the global village
IT security small business leaders have to deal with a lot of data points and business decisions everyday. One of those business decisions is new business development and contracts. Whenever IT security business is looking at new business they always come across the traditional "low-baller" or "time-waster" or "predatory" person selling non-existent IT security opportunities. You can read about those at James blog here.
These persons are also dangerous to your business because they take your personal information and transmit that to different parties. Since most of these body shops are located in SE Asia without any understanding and respect for Western small businesses, their low rates and constant emails and calling is a burden to your small business. Once you get on their mailing list, it is next to impossible to "opt-out" of their mailing list. I hope congress can categorize these time wasters in the same category as spammers. More on these scam artists and predators here.
All small business leaders have to deal with such dangers every day and have acquired skills to avoid wasting time on such hopeless endeavors.
These persons are also dangerous to your business because they take your personal information and transmit that to different parties. Since most of these body shops are located in SE Asia without any understanding and respect for Western small businesses, their low rates and constant emails and calling is a burden to your small business. Once you get on their mailing list, it is next to impossible to "opt-out" of their mailing list. I hope congress can categorize these time wasters in the same category as spammers. More on these scam artists and predators here.
All small business leaders have to deal with such dangers every day and have acquired skills to avoid wasting time on such hopeless endeavors.
Subscribe to:
Comments (Atom)